The Art of Finding Ghosts: How Deleted Data Lives On
A Deep Dive into Archived and Forgotten Web Content
(A brief message: I am trying to get back into writing blogs and sharing thoughts and knowledge I have around OSINT, Red Team & Pentesting. This blog is not very detailed as I am still trying to figure out how my own site works.)
Introduction: A Telegram Post That Shook a Private Army
August 2022, At the height of Russia-Ukraine War, a Russian war correspondent deeply entwined with Kremlin ambitions and affiliated with Wagner Group posted photos of what seems to be, a base in Popasna, a Russian occupied town in Eastern Ukraine. Specifically, it showed photos of soldiers, military equipment, and one subtle detail: a building entrance marked with a street sign reading Mironivska Street, 12 in Popasna, Ukraine.
The message was deleted just hours later but the post was archived. Investigative journalists and OSINT researchers began dissecting every pixel.
Few Days later, Ukrainian forces launched a devastating HIMARS strike, allegedly obliterating the Wagner base the photo revealed.
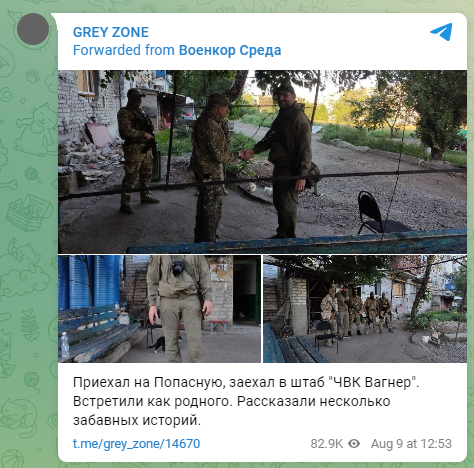 The now deleted Telegram Message (Source: Mark Krutov (Twitter/X))
The now deleted Telegram Message (Source: Mark Krutov (Twitter/X))
This wasn’t just a tactical military failure, it highlighted a symbolic moment in modern asymmetric warfare. An entire command center, exposed not by leaks or spies, but by the group’s own media propaganda. The digital ghost of a deleted post turned into a lethal vulnerability.
The Wired article shows how the fragments of open data such as, images, addresses, metadata, can create a mosaic sharp enough to direct precision firepower. This showcases the modern battlefield: one where information is not only a weapon but a liability.
The speed at which this post vanished, and the lack of any reliable archive, speaks volumes about the growing OPSEC awareness among state-aligned actors. But as we have seen in the past, even a few minutes online can be enough for an analyst to trace a target.
Ghost Data: Why Deleted Doesn’t Mean Gone
In an time where deletion is often assumed with permanent erasure, the Wagner incident is a textbook example of how data that’s meant to vanish often survives in dangerous ways.
Caches and Snapshots
Tools like Archive.today, the Wayback Machine, or even Google Cache routinely snapshot public web content. Once something is published, these tools may already have mirrored it and its often faster than deletion.Automated Archiving Bots
While many previously active bots like @uriminzok and @Gerjon_ are no longer posting, they played a crucial role in archiving volatile content. As these fade, the OSINT community must build or maintain its own archival pipelines.Crowd-powered Forensics
OSINT communities on Reddit, Discord, and Twitter thrive on challenge-response loops, where a user posts a clue, and the swarm uncovers the rest.
The Popasna example underscores a chilling point:
The failure wasn’t in Russian encryption or battlefield secrecy, it was a human behavioral failure. Someone trusted to post propaganda content did so with just enough detail to unravel an entire facility’s location.
OSINT Tactics Used to Identify the Wagner Base
Here’s how researchers likely exposed the base location using only open sources:
- Visual Clue Extraction
- The image showed a street sign:
ул. Мироновская, 12(“Mironivska St. 12”). - Analysts enhanced contrast, zoomed, and isolated Cyrillic text.
- The image showed a street sign:
- Satellite Imagery Matching
- Tools: Google Earth, Sentinel Hub, Terraserver, Planet Labs.
- Analysts matched building structure and layout to existing city imagery.
- Temporal Correlation
- Using SunCalc, they examined sun angles and shadow lengths to estimate when the photo was taken.
- Strike Confirmation
- Post-attack satellite images revealed HIMARS-compatible destruction.
- Analysts matched the structural damage to the geolocated site.
All of this occurred in public. No intrusion, no classified leaks, just pure rigorous analysis of ghost data by Intelligence Analysts and OSINT Researchers.
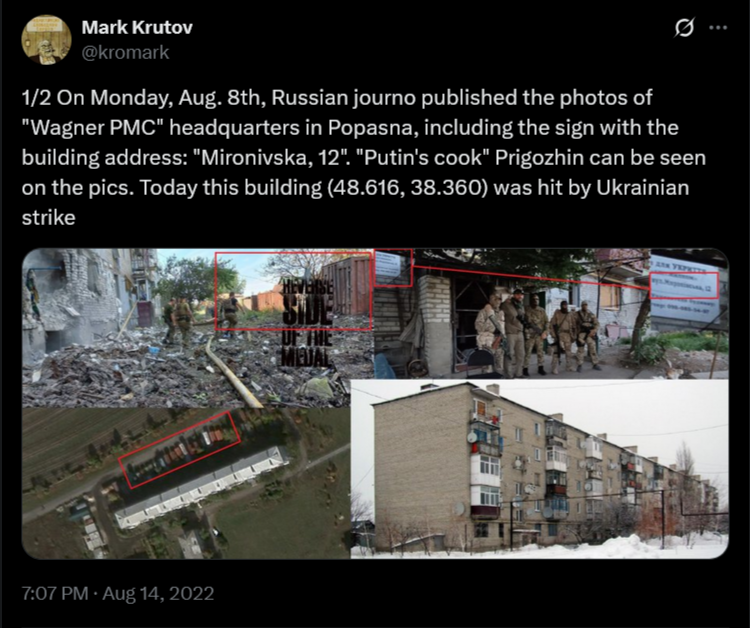 Mark Krutov did a great deduction of images in this Twitter Thread
Mark Krutov did a great deduction of images in this Twitter Thread
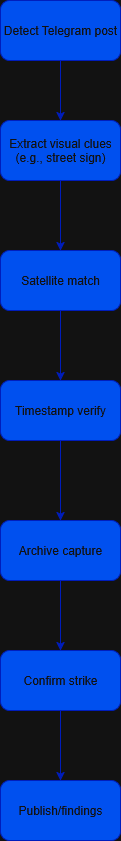 A generalised workflow for gathering archived information
A generalised workflow for gathering archived information
What Makes Ghost Data So Powerful
The real danger of ghost data isn’t that it exists, but that it persists long after it’s forgotten. Its strength lies in its context:
Behavioral Forensics
Time of post, language, sentiment, and platform use help build user profiles.Operational Leakage
Backgrounds may contain maps, insignia, or monitor reflections.Geo-imprinting
Soil color, vegetation, cloud patterns. All minute details can tie images to locations.
In Popasna, the Wagner Group was not undone by cyberwarfare, it was outflanked by its own content.
Tools for Recovering Deleted or Hidden Data
| Tool | Use Case | Link |
|---|---|---|
| Wayback Machine | Archived web snapshots | archive.org |
| Archive.today | JS-heavy page archiving | archive.today |
| Google Cache | Recently cached pages | cache:<url> in Google search |
| SunCalc | Timestamp via shadow analysis | suncalc.org |
| Sentinel Hub | Satellite imagery and layers | sentinel-hub.com |
| TruffleHog | Git history secrets | trufflesecurity.com |
For locating images or archived Telegram posts, you can try:
Telegram Archive Search by CQCore
Reverse image search via Yandex or Google Images
Public Telegram archive aggregators such as tgstat.ru or @tgdb_bot on Twitter/X.
What the Wagner Case Tells Us About OPSEC Today
Everyone Is a Source: Whether it’s a soldier, influencer, or bystander. Anyone with a phone becomes a potential threat to secrecy.
Propaganda Can Backfire: Messaging designed to inspire or intimidate can turn into evidence.
Deletion Is Not Disappearance: If it has been published, someone likely saw it, scraped it, or archived it.
Closing Thoughts: The Battlefield is Now Semantic
The Wagner incident is more than a mishap, it’s a warning about today’s battles, and how information flows faster than bullets. A misstep online can destroy lives offline. The most devastating modern strikes aren’t always guided by satellites or insiders, it can be guided by a sign on a building in a now-deleted post. In the fog of war, silence isn’t just discipline. It’s survival.
In this digital arena, ghost data is like radioactive fallout. Invisible, persistent, and increasingly weaponized. What used to be secrets passed in shadowy rooms are now mistakes posted in daylight. And the best intelligence doesn’t always come from hacking. It comes from paying attention.
Written by Argonyte
References: Wired (2023), Archive.org, Sentinel Hub, Google Earth, OSINT Twitter/X Community